Cloud Security
What is Cloud-Integrated Security?
Traditional Video Surveillance and Access Control systems use on-site servers running application-specific software supporting video management and access control devices. In a cloud-based system, the management software is in the cloud eliminating the need to purchase and maintain server(s) and software for your security systems. Providing peace of mind that your system is not dependent on the operation of a local server and that your security software is always up to date.
Why Cloud-Integrated Security Systems are Beneficial
Cloud-based access control can be extremely cost-effective, by removing the need for expensive physical servers, as well as making physical access cards unnecessary by allowing smartphone credentials to be used. Costs associated with cloud-based systems are typically a monthly per device cost, which provides greater flexibility in budgeting pricing for your system.
An added benefit of these cloud-based systems is that your system is easily scalable, allowing for the level of integration that you require for your facility. As new cameras or secured doors are added to your facility, you can easily link them through the web-based management application.
Additionally, all of this can be managed through a web-based application that can be accessed on a desktop or mobile device, meaning that you do not need to worry about having software installed and updated to be able to manage your facility remotely. Cloud-based system providers will typically use the most current tech and implement best practices when it comes to cybersecurity threats. Your systems will always be up to date and will not choke your networks bandwidth to properly operate.
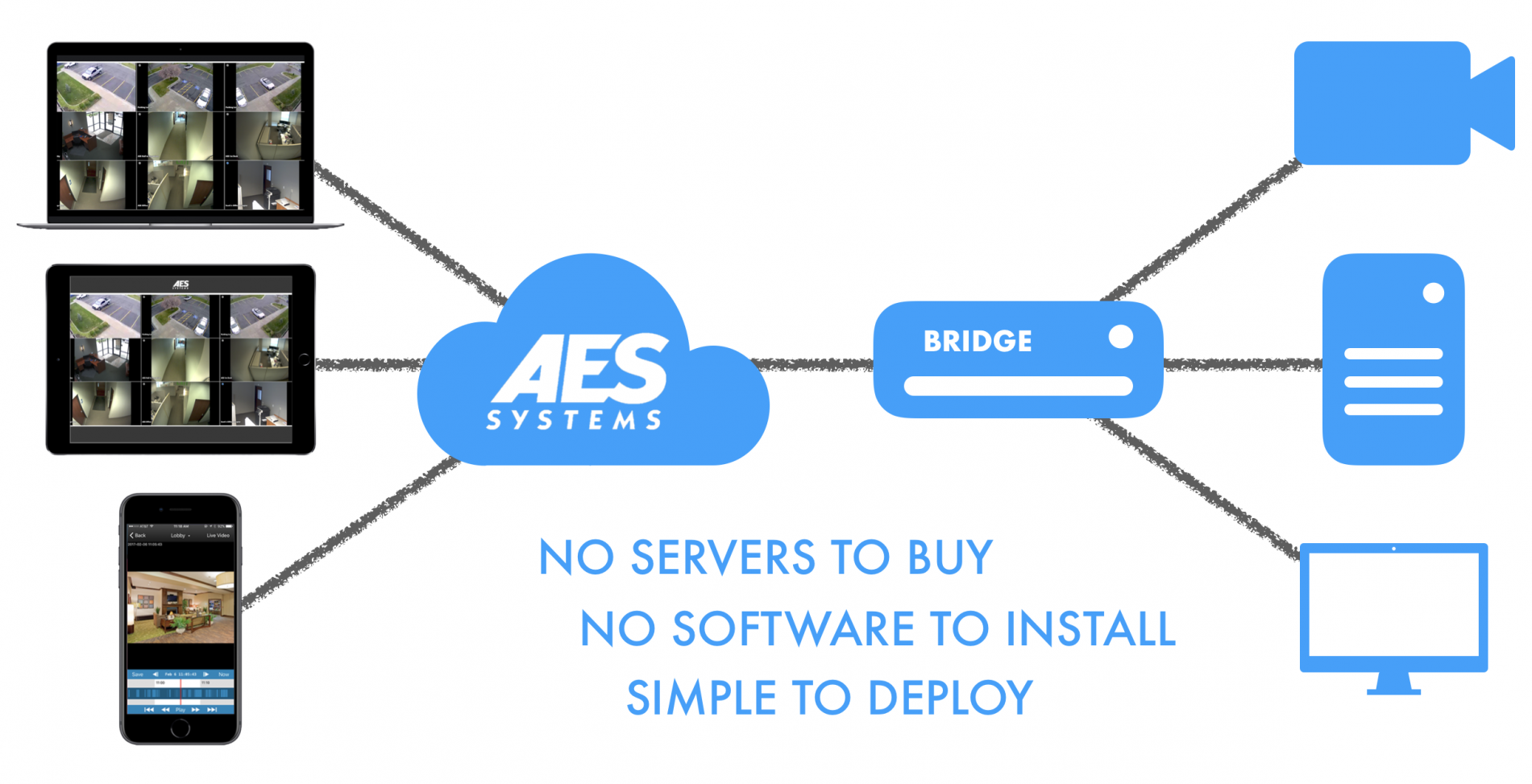
How it works
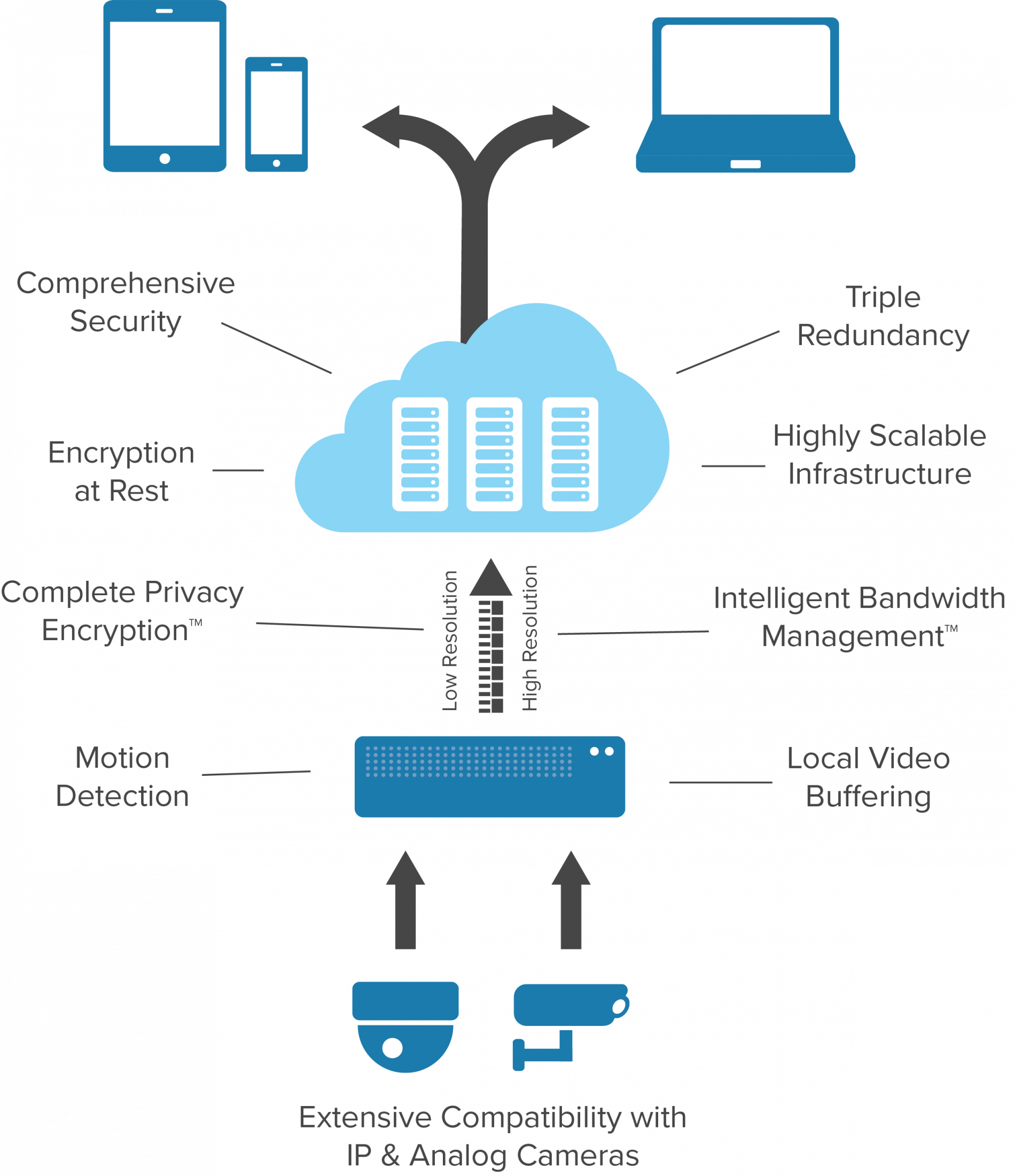
Secure and Protected Data
Video and other data from your cloud-based systems are uploaded directly to the cloud and housed within highly secure data server sites. Since this data is stored off-site, your video recordings and access control databases are protected from physical damage, hardware defect and theft that may occur with on-site servers at your facility. This will provide greater protection for your data.
Simplified Installation and Maintenance
With cloud-based systems, there is no need for IT personnel to help maintain and troubleshoot on-premises servers, while updates are automatically deployed to your system, ensuring that you can immediately benefit from new features and tools. Easily delivering new features and functions without impacting operations and routine tasks.
AES Systems can help design and install your cloud-based security system. Be it video surveillance or access control systems, AES can provide you with on-site or remote assistance to ensure that your system has been optimized for your facility.
Multi-Site Monitoring Access
Cloud-based systems allows you to view and monitor your cameras, access control doors and all related hardware locations from a single intuitive application, making it a highly effective solution for franchise and multi-site business owners to extend their visibility across all operations. This will allow you to view live and recorded video from any device connected to the internet, including your laptop, smartphone, or tablet.
Multi-location systems will also save on the cost of purchasing and maintaining expensive equipment for each location, further reducing the cost over the long run.
Key Benefits Highlights
- Record and view video in the cloud, eliminating the need for on-site servers. (Light on-site hardware footprint)
- Rapidly deploy IP cameras and access control devices with minimal configuration required
- System software patches, hotfixes, firmware, and maintenance deployed automatically
- Subscription-based services allows greater budget flexibility
- Flexible administrative/user programming
- Ability to secure remote locations with only a cellular connection
At AES Systems we can help design and integrate the needed hardware and components for your cloud-based security systems. AES has partnerships with the leading manufacturers and distributers to provide our customers the latest innovative solutions and with the most competitive price. With a vast resume of past and current projects AES can navigate through complex problems and provide the best solutions for its customers.

